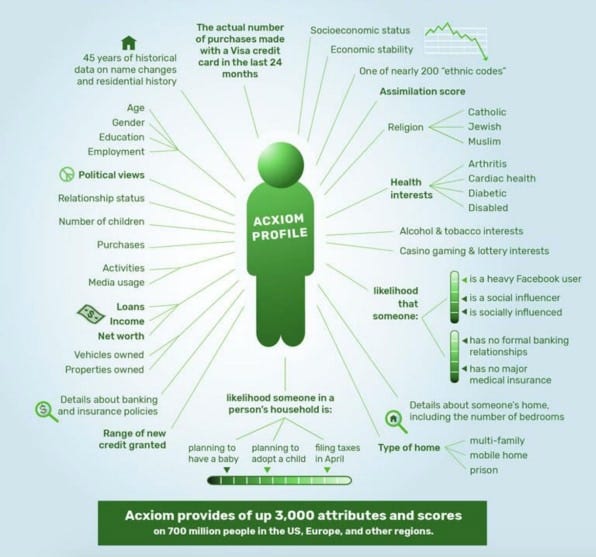
6 Ways Big Tech Collects, Then Uses Your Data
Why you should care and what you can do about it
NOTE: You can sign up to be among the first to test our new privateLINE.io service HERE. This service keeps your communications off the internet in your own private enclave without data collection or tracking.
When phones were copper lines and connected to your local Telephone Company, a warrant was required to listen in on conversations. Only criminals were wiretapped — that was what we were told. With the advent of mobile phones and wireless services, a Big Tech layer has been added on top of your phone and internet line — when you click “I agree” to the Terms of Service agreement, you give Big Tech and others permission to collect and use your data. Each app on your phone can have permission to collect your personal data, so long as “You Agree”. No warrant is required if you give permission to share your data, and it can be resold to anyone, including law enforcement.
Your data is being collected everywhere on the internet by thousands of tech companies and application developers, making your private information available to almost anyone who can pay for it.
Multi-billion $ industries are based on your personal and business information. If this data wasn’t valuable, their services would not be free and those companies would be worthless. If you knew all the ways your data was being used, you would not be happy. It turns out you are worth quite a bit of money to someone, or maybe they just want to keep tabs on your whereabouts. With vast, low-Earth orbit satellite fleets covering the Earth, there will be no escape from the surveillance. Here’s a recent story about how the NSA is buying your data from data brokers without a warrant:
SAN FRANCISCO, Jan 25 (Reuters) - The U.S. National Security Agency buys Americans' internet browsing information from commercial brokers without a warrant, the agency's director told Democratic Senator Ron Wyden in a letter made public on Thursday.
Wyden, who released the Dec. 11 letter, called upon U.S. intelligence officials to stop using Americans' personal data without their express knowledge and consent, saying it was unlawful.
There are about 4,000 active data brokers who resell data:
Look carefully. By aggregating data from many sources, a complete picture of almost anyone can be computed. Source: CrackedLabs.org
Let’s think for a minute. If you gave your permission for someone to collect and use your data according to their terms in an app or device….can’t they legally do with your data as they wish? What about information gathered from public places? Like CCTV on the street? What about grabbing unencrypted comms like email from the open internet? (Note: your email is relayed using plain text after it hits the first relay server, the encryption is only from your software client to your server). There are clear court cases in the USA where there is “No Expectation of Privacy in Public”. This is actually a good thing for society, it keeps things in public open and transparent. But where your data is concerned, you need to maintain internet situational awareness and take care or it could end up in the hands of data brokers.
Someone is buying your information or access to you based on your real time location, who you communicate with, your emails and proximity to others. Everything you type on or say near your phone can be captured. This data collection might be illegal in some places, but remember, once you give someone your permission to do it, it’s 100% legal. After all, it’s your information and you agreed in the Terms of Service to grant them access to it.
Let’s track the data collection and see where it’s going and what you can do to minimize what is collected.
Some people think “I’ve got nothing to hide and nothing to worry about”. Data collection started with security agencies, who have always tracked people of interest for internal and external threats. This was imitated by advertisers and Big Tech, who were financed and advised by these agencies and now collect information on everyone (not just potential threats). The security agencies now have access to a wildly broader source of data that has been collected by Big Tech with permission from…YOU. Now, China, using technology provided by Big Tech, leads the way with a comprehensive social credit system based on the gathering and use of this personal data. A social credit score entirely influences how you are able to interact with society - from transportation to banking, for starters. In China, CCP Party functionaries are rewarded and good people are punished. Also, there is substantial industrial espionage and business interference happening you need to be aware of. I’ll show you one solution we have been developing to create your own Safe Space away from the internet and the intrusion of Big Tech — we call it privateLINE.
privateLINE is a private network that functions like the internet, but away from the internet. We create an encrypted tunnel from your computer to a secure enclave and give you communications applications that only work in the private enclave. You can find out more about it at privateline.io CLICK HERE. We are beginning the ALPHA service and you can click through to the website, then click on any of the “Get…” or “Try…” buttons to sign up to be on the waitlist to try it out.
Data is only valuable when it can be turned into “actionable information”. There are laws about government data collection, but if you enter into a private agreement with Big Tech via CLICK TO ACCEPT, you might have agreed to let them exploit your data extensively. Many of these info gathering techniques originated with security services, but now corporations are in on the act and because you agreed to everything, it is 100% legal. After all, you accepted their terms in exchange for watching a video or using some software. They are after your IP address wherever it appears, your location, as well as any associated phone numbers and email addresses, not to mention whatever subject you are talking about. This happens because the companies that purchase your data will then be able to market products and services to you.
Did you know your conversations are recorded, processed and scored with AI in real time and added to your file? Out in the field at The Ranch, I had a conversation with one of our contractors about a concrete pad. My Android phone was in my pocket and 20 minutes after going inside, I started getting Google Ads for “concrete pads”. Extremely spooky. Everything you say in front of the microphones is being recorded and potentially sold or worse.
The solution is to move away from the internet and keep a private side to your life. You can still maintain a public presence while keeping certain things private. Check out privateLINE for one solution to this problem.
Everything is highly automated with AI and data is collected from:
Networks - Phone carriers and ISP’s have your location, frequency, meta data and frequency with whom you are talking to, which websites you visit and your IP (internet address), phone, email and other data you willingly provided them when you agreed to use their services. Your data also travels over the open internet for things like email, website visits and many other things. These networks not only cooperate with state security agencies (they have to, they are not given a choice — there is really no escape from state security when using public wires or spectrum), but your data is also “brokered” and resold by private companies you willingly gave your data to when you accepted their “Terms of Service”.
We are all subject to having our data accessed by leaks over the internet. For example when you send an email, while it is encrypted on the first hop, your message is sent via plain text for the next dozen mail server relays. Hurricane Electric is a CCP controlled company, it has ~19% of the public internet IP prefixes, so they have control over those IPs. Anything going through a router controlled by companies like this should be assumed to be “phoning home your data” to Beijing. The CCP is doing the same thing every state security service does everywhere, including our NSA and CIA.
The notorious Room 641A at ATT. The NSA “legally” tapped into all internet communications going through the main ATT switch in San Francisco. The internet is a PUBLIC space and in the USA, there is no expectation of privacy in pubic. Rooms like this are installed at most data centers and telcos in the USA, as well as in other countries. This is why you need a Private Network. Photo credit: Wikipedia.
Hardware - Everything runs on hardware and software. Backdoors have been built into nearly every commonly available hardware CPU. Extra goodies also get installed in your hardware on the way from Amazon to your front porch, if you are targeted in any way. Intel, AMD and ARM processors all have an “administrative area”, accessible by wifi and 3G cellular right on the CPU, in addition to whatever network connection you thought you turned off. This is very difficult to avoid, unless you use 15 year old hardware or a custom chip that can be fully audited and secured. This hardware vulnerability can be found on phones, routers, appliances, doorbells, security and traffic cameras, etc.
Operating Systems - All the major OS have issues. Windows, Mac and even Linux have zero day exploits (unreported flaws that can be hacked) and back doors. A new OS or even one that is cleaned up would be a major undertaking.
Applications - Tik Tok is the most obvious offender, but many free applications also track and sell data. When you click “Agree” to let them use your mic, they could be recording you everywhere and sending back data. Mics are very sensitive, they can hear your conversation up to ten offices away. Many applications included with mobile devices do this out of the box. We tested a new phone from China and it was sending 100MB of data per day from 20 different apps we had not even used! Beware!
NOTE: You can sign up to be among the first to test our new privateLINE.io service HERE. This service keeps your communications off the internet in your own private enclave without data collection or tracking.
Internet of Things - Appliances, TV’s, cars and anything with electricity can have hidden trackers and microphones. Data is returned via IoT cell networks, which are completely separated from the internet. China was caught grabbing this data in the USA and nothing was done about it. You have to assume the NSA was making a copy for themselves and their “partners”.
Here are some of the most obvious ways your information is collected.
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart). Proving you are not a robot is one thing, but every time that cute grid pops up, your IP address goes right to Google’s Data Centers. Let’s say you are using a certain web site, or app, as soon as the CAPTCHA screen loads — your IP address will be appended to your record at Google. CAPTCHA is so ubiquitous it’s become a meme:
Facebook - Facebook is a spying machine that was originally known as Lifelog (created by the CIA), before becoming Facebook. You are tracked through both your “private messages” and what you post on the Facebook site, they also track your visits on other sites with their tools on other sites, such as commenting, buttons and other syndicated features.
Facebook spying is so widespread humorous memes have been created about it.
Google - Probably the greatest spy machine ever devised, it tracks you nearly everywhere on the internet, and it also tracks your phone’s location, microphone, camera, photos (with GPS embedded), videos. The microphone routinely listens as long as the phone is turned on and even while it’s sitting unused in your pocket. As mentioned above, I had a conversation with a contractor and twenty minutes later I was getting ads for “concrete pads” (I had only mentioned it to him), never in any email. Google controls 84% of internet search, and much of the web site authentication and tracking. Analytics is used on most sites and all your web site visit data is grabbed there.
Single sign on has been the holy grail for Big Tech. They know every app and web site you have joined and how often you visit when you click on their icon “for convenience”. There is often a price for one click convenience.
Zoom video conferencing - Assume everything on Zoom goes back to China and they collect all calls, chats and contacts you are communicating with. Even though they claim to have “cleaned up” these reported problems, it shows a lack of care and you should avoid this app. Don’t take my word for it, this has been very well documented:
Zoom Gets More Popular Despite Worries About Links to China
Zoom Traffic Through China: Company Apologizes, Announces You Can Control Data Routing
STOP using ZOOM or risk being WATCHED by the Chinese Communist Party (CCP)
Your car - Mozilla and Electronic Frontier Foundation (EFF) did a study of data collected by cars, here is what they found: “Mozilla breaks down four main reasons why it finds car privacy (or lack thereof) so concerning. They are;
They collect too much personal data (all of them)
Most (84%) share or sell your data
Most (92%) give drivers little to no control over their personal data
We couldn’t confirm whether any of them meet our Minimum Security Standards
Perhaps the most concerning aspect of the study is that each car brand Mozilla tested failed miserably in the privacy test. The foundation finds that cars are collecting more data than necessary for driving, and cars are in a unique position to collect a lot of data about you, since they take you almost everywhere.
"They can collect personal information from how you interact with your car, the connected services you use in your car, the car’s app (which provides a gateway to information on your phone), and can gather even more information about you from third party sources like Sirius XM or Google Maps. It’s a mess," the study says. Additionally, over half (56%) of car brands tested will share your data with government agencies or law enforcement from a simple request -- not a formal one. 84% of those tested will share your data, and 76% can sell it.
It goes beyond just the data from your car and how you drive; how often you speed, the number of “near misses” you had including “hard braking”, etc. That info will be fed to your insurance company and affect your rates. That oil change or any maintenance you just got, the shop records the mileage and that gets sold to the data brokers.
The takeaway here is that, if you drive a modern car with smart capabilities such as trackers, sensors, camera, and preinstalled apps, it's probably tracking you.” What can you do about it? Drive an older model car. The data collection is built deep into the electronics and it will be difficult to untangle things.
Household “Smart” Devices - Your doorbell camera and household devices (Roomba, Alexa, etc) are sure handy, but most are data vacuums, in addition to whatever dirt they clean off your floor. Anything with a camera or microphone can be turned on at any time to listen or watch what’s going on around it. The Ring cameras are quite popular, but who has access to them?
In some cases, yes. Ring says that it will still cooperate with law enforcement when a search warrant is present, and Ring still has the right to share user data without consent. Ring said in an interview with The Verge that police can request footage in “emergencies” without obtaining a search warrant—making when and how law enforcement obtain footage arguably less transparent than before. I guess it depends on what kind of emergency the police are having….
Those robo vacuums make nice maps of the inside of your home, in addition to keeping things tidy.
High-end models of Roomba, iRobot’s robotic vacuum, collect data as they clean, identifying the locations of your walls and furniture. This helps them avoid crashing into your couch, but it also creates a map of your home that iRobot could share with Amazon, Apple or Google.
And when it comes to Alexa, it’s always listening (if only for the word “Alexa”). The UK Sun reported the surprising sounds that triggered Alexa:
A SUN investigation today reveals Amazon staff can listen to Alexa recordings of British couples rowing, discussing private family matters — and having sex. The sounds of lovemaking are among noises that can trigger Alexa-activated Echo speakers, which make recordings as users speak to them.
Your phone - This is the big one. People carry their phones everywhere. Your phone has a number of ways it can be used to spy on you with the microphone, camera, gps location, and other sensors. This data can reveal many things about you. It used to be you could remove the battery from your phone if you wanted privacy, but that is no longer an option. Batteries are locked inside phones to save on manufacturing costs. The best way to gain privacy is to put the phone out of earshot, which is not easy since phone microphones are very sensitive. A friend was told by someone in a security agency “phone mics can hear everything ten offices away”. We need to be careful. Apps are also spying on you using the sensors and anything else you give them permission to do.
Most people don't know that by installing a phone app you agree to terms beyond what you may think you agreed to. One example is thinking you're just allowing an app to access your photos. "They don't realize that also included in the things they agreed to are their browsing history, their search history, things they purchased, financial information, health and fitness data," she said.
A few years ago, another study was done on how much data was being collected:
New research conducted at Carnegie Mellon University asked 23 users of Android’s version 4.3 to use their smartphone, and tracked requests for location data from each device with specially designed software. The study revealed that many popular Android apps tracked their user nearly 6,200 times per participant over two weeks – that’s every three minutes. The study found that apps asked for more data than was needed. The participants received daily messages telling them how many times their personal information lists had been shared, and some privacy nudges were particularly alarming. For example, over just a few days your location could have been shared 5,398 times with Groupon, Facebook, and more. One participant reacted to these nudges by saying that he felt like he was being followed by his own phone. The amount of location information shared can be quite alarming.
That there is a mountain of data on you collected every day should not be surprising, and once it goes to a data broker, it will be sold to anyone with money.
NOTE: You can sign up to be among the first to test our new privateLINE.io service HERE. This service keeps your communications off the internet in your own private enclave without data collection or tracking.